Here’s How Phone Number Can Destroy Your Whole Life!

How Phone Number Can Destroy Your Whole Life? You may think your Social Security or bank account numbers are the most delicate digits in your life. These days, hackers can do more harm with little effort using just your cell phone number.
In some situations, giving your digits to organizations like your bank gives an additional layer of security.
But in most cases, the potential risks and irritations of issuing your number surpass the advantages, as you will read below.
What's more, it requires surprisingly little effort to destroy your online life.
HOW YOUR PHONE NUMBER EXPOSES YOU?
It took just an hour for your cellphone number to uncover your life. The Hacker, needed to do was plug your number into White Pages Premium – an online database that charges $5 every month for access to public records.
He then did a careful web search and followed a data trail — connecting your name and address to data in other online background-checking tools and public records — to find more details.
HOW DO HACKERS STEAL CELL PHONE NUMBERS?
It's simpler than you may suspect. Phone numbers can be found anyplace – thanks to a limited extent to such a significant number of data breaches.
Often, hackers will discover the cell phone number of their target gliding around the web (or from a phone bill in the trash), and call up their transporter copying the customer.
With a couple of simple inquiries replied — negligible more than where an individual lives or their date of birth, they ask the customer service representative to "port-out" the phone number to an alternate transporter or a SIM card.
That is it. When the "port out" finishes, the phone number initiates on an attacker’s SIM card, and the hacker can send and get messages and make calls as though they were the individual they just hacked.
Much of the time, the main sign that it happened is if the victim suddenly loses cell service for no apparent reason.
From that point, it's as simple as starting password resets on accounts related to that phone number. Facebook, Gmail, Twitter — and the sky is the limit from there.
A hacker can utilize your hijacked phone number to steal all of your digital currency, adopt control over your vanity Instagram username or maliciously delete all of your data.
You can read what happened to TechCrunch's (very own John Biggs ) when his phone number was hijacked.
In the worst cases, it tends to be difficult or impossible to recover your phone number — not to mention the accounts that get broken into. Your most solid option is to ensure it never occurs in any case.
AFTER GETTING NUMBER, THIS WHAT CAME UP!
Your current home address, its area, the expense of the property and the taxes you pay on it. Your past addresses from the recent decade. The complete names of your mom, father, sister, and auntie…
Your past phone numbers, including the landline for your parents’ home. Data about a property you recently possessed, including its area and the home loan is taken out on it. Your absence of a criminal record.
While Hacker declined to hack into your accounts utilizing the obtained information and number, the organization cautioned that there was plenty an attacker could do:
- #1 Swating – This is when an individual calls police to report a crime being committed and direct them toward the address of a target they need to threaten. Police appear and treat everybody at the house as a potential criminal. Not great.
You needn't bother with a telephone number to SWAT, because emergency services don't stress over whether it's genuine or a trick.
You call and give an address and they appear and they appear in force. A SWATer can simply call and state it's a neighbor's address.
SWAters takeoff their telephone numbers thus they can't be traced. Spoofing is getting honestly normal with the development of VoIP service.
But if the SWATer can spoof the telephone number as the spot that is reporting the crime it will give a more prominent faith this is a real crime.
In other words, calling and saying crime is being committed at 20 Maple Lane and 20 Maple Lane appears at the 911 agency as the calling address, at that point it includes an additional level of confidence.
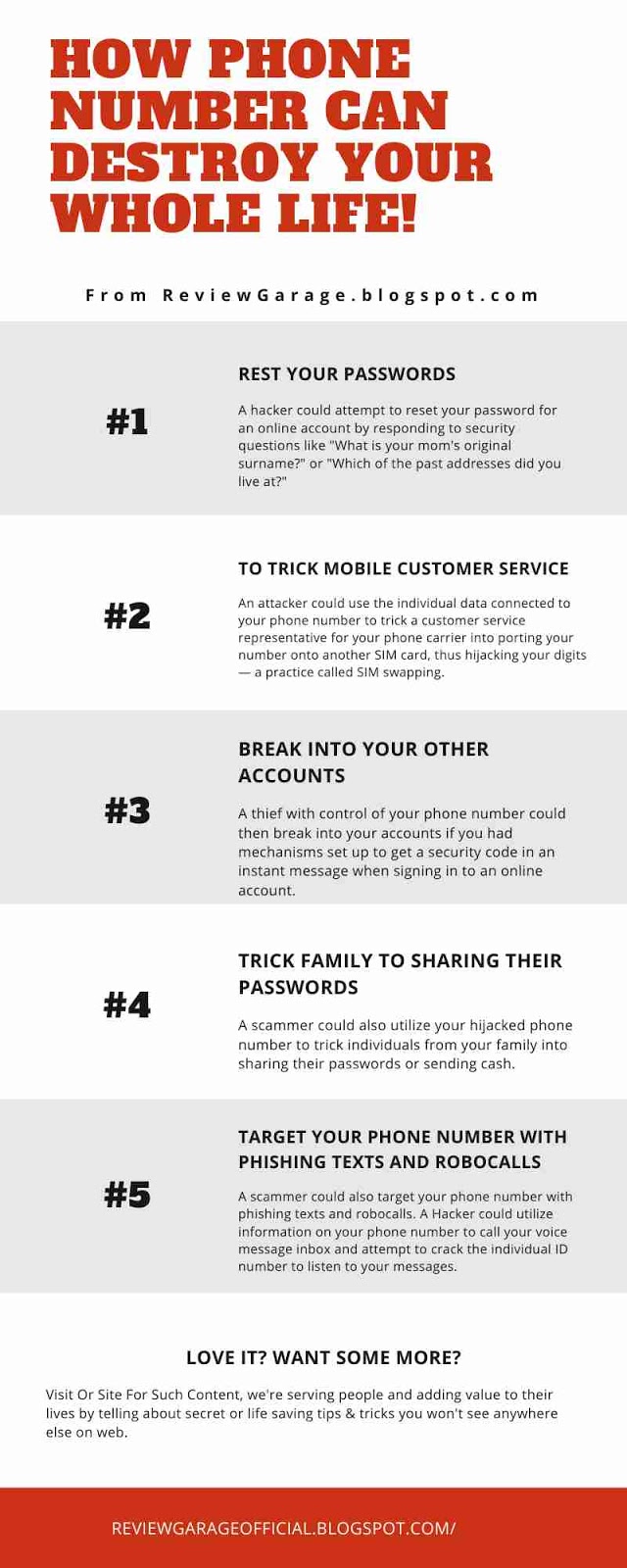
- #2 A hacker could attempt to reset your password for an online account by responding to security questions like "What is your mom's original surname?" or "Which of the past addresses did you live at?"
- #3 An attacker could use the individual data connected to your phone number to trick a customer service representative for your phone carrier into porting your number onto another SIM card, thus hijacking your digits — a practice called SIM swapping.
- #4 A thief with control of your phone number could then break into your accounts if you had mechanisms set up to get a security code in an instant message when signing in to an online account.
- #5 A scammer could also utilize your hijacked phone number to trick individuals from your family into sharing their passwords or sending cash.
- #6 A scammer could also target your phone number with phishing texts and robocalls. A Hacker could utilize information on your phone number to call your voice message inbox and attempt to crack the individual ID number to listen to your messages.
HOW MARKETERS TAKE ADVANTAGE?
An advertisement tech organization could add your number to a detailed profile about you, connected to other data about my identity and web-browsing activities.
On the off chance that you signed up for internet service with your phone number, a brand that purchased your digits from an advertisement firm could transfer them into a promotion tech tool to relate the number with your online profile and serve targeted ads.
A shady marketing agency could add your number to a database to blast me with spam calls and ads.
WHEN AND HOW TO SHARE NUMBER (AND WHEN NOT)
There are some situations when sharing your phone number is sensible. When you enter your user name and password to get into your online banking account,
The bank may call or text you with a temporary code that you should enter before you can sign in. This is a security mechanism known as a two-factor verification/check.
In this situation, your phone number is a valuable bonus factor to prove, you are who you say you are.
A phone number is a better identifier than just your name, yet sometimes you need that,
– Said Simon Thorpe (director of product for Twilio, a communications company, works with phone bearers on battling robocalls.)
In any case, which organizations would it be advisable for you to trust with your phone number? Here's the place things get tricky.
A lot of tech companies let you utilize your phone number to shield your accounts from unauthorized access.
But even some authentic brands like Facebook have been examined for inappropriate utilization of phone numbers.
A year ago, a study by the tech blog Gizmodo – found that after a Facebook user set up two-step verification with his phone number, sponsors that uploaded his digits into Facebook's database could direct them to his Facebook profile and serve targeted ads.
Separately, some people complained this present year that the social network allowed them to look into an individual's Facebook profile just by typing a phone number into its search bar.
The company has removed the capability to discover individuals' profiles by entering their phone number, She included that when a user set up two-step verification with a phone number, the company would not utilize the data to serve targeted ads.
– Said Rochelle Nadhiri, (Facebook representative).
HOW TO PROTECT YOUR CELL PHONE NUMBER?
Assuming you have your solid passwords set up and your two-factor authentication set up, you think your accounts are currently protected? Think again. There's considerably more to be finished.
But unlike your Social Security number, you're far less likely to keep your cell phone number a mystery — generally, no one can get in touch with you!
Regardless of whether you're an AT&T, Verizon, Sprint or T-Mobile customer, each cell phone number can be a target for hackers.
You may think your Social Security or bank account numbers are the most delicate digits in your life. These days, hackers can do unmistakably more harm with little effort using just your cell phone number.
CONCLUSION

Your cell phone number is a single point of disappointment. Consider it. You use your cell phone number constantly. You use it when you join sites and services, and sometimes you'll utilize it to sign in to an application or a game on your phone.
If someone steals your phone number, they become you — in every way that matters. With your phone number, a hacker can begin hacking your accounts one by one by having a password reset sent to your phone.
They can trick companies security — like your bank — into believing they're you when you call customer service.
What's more terrible, they can use your hijacked number to break into your work email and documents — potentially exposing your employer up to data theft.
Simply think about each site and service that has your phone number. That is the reason you have to ensure your phone number.
Much the same as you can apply two-factor authentication to your online accounts, you can add an optional security code to your cell phone account, as well.
Moreover, You can call customer services or do it online.
You can ask customer service, for instance, to set a secondary password on your account to guarantee that only you — the account holder — can make any changes to the account or port out your number.
Each transporter unexpectedly handles optional security codes. You might be restricted in your secret phrase, password or passcode, yet attempt to make it more than four to six digits. And make sure to keep up the backup of codes!
So, are you securing your phone number?, I’m curious to know whether you shared your number without any hesitation?, Comment down your answers!




![Microsoft All In One App Out Now! [Download Link]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjCvr2abWBSOGGuor1TDujjOinz955lWrv9r9DTODl34TFpdX67fG7tN5i1632u5IVgBAqIKGSLnjzBgDqnOkkoU9o-pNZV7ta9iV-4NjVLi6FP0dpVjWYHXbRI18WQcMY6WLeOGnhJVPA/s72-c/microsoft-office-ios-preview-setup.png)



No comments: